When Microsoft released the Xbox 360, it was designed to be unhackable. Security-wise, the machine was a step up from the original Xbox with custom hardware and encryption keys to keep hackers and modders at bay. Of course, they figured out an in, but what makes this exploit for the Xbox 360 Slim so wild is that it was done with a drill.
Yeah, you know. A drill.
The original Xbox and its rival the PlayStation 2 could be modded by soldering chips directly to the circuit board and by adding these chips, copyright measures were removed. It was then possible to run bootleg discs, explained the BBC back in 2005 in an article detailing Microsoft’s plans for a then-new unhackable machine.
“We’ve taken security to the hardware level and built it in from the ground up,” Chris Satchell from the Xbox Advanced Technology Group told the BBC at the time. “There are going to be levels of security in this box that the hacker community has never seen before.” But Microsoft was not naive. Exploits were inevitable. “I’m sure sooner or later someone will work out how to circumvent security,” said Satchell. “But the way we have done the design doesn’t mean that it will work on somebody else’s machine.”
In a recent video, YouTuber Modern Vintage Gamer recounts the anti-priracy measures Microsoft went to prevent Xbox 360 hacks, such as stealth media checks, Xbox Live bans, and even encrypted firmware. So to flash a custom firmware, thereby making modding possible, it was necessary to unlock the DVD drive. Hackers targeted the flash chip on the DVD board as their way in.
But what makes the Kamikaze Hack so interesting is the extent hackers went to circumvent the console’s security. When Microsoft released the new slimmer Xbox 360, the company replaced the flash chip, and instead combined it with the digital signal processor chip into a single MediaTek chip package that could not be easily flashed with custom firmware. This made it harder for hackers to isolate the flash chip and hack the console. Microsoft also went one step further and encased the chip in a resin for good measure. To open up this drive for flashing so that the console would run custom firmware, it was required to drill a hole in the chip to disable the protection. Software tools alone would not work.
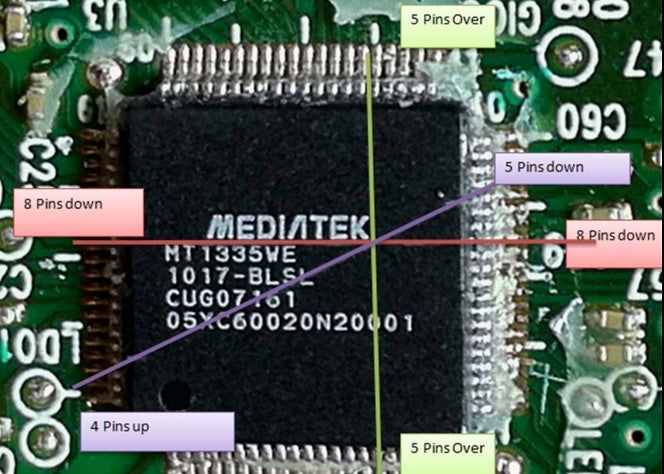
“Microsoft thought this would be enough to stop hackers dead in their tracks,” said Modern Vintage Gamer. It was not.
After removing the chip’s cap and seeing what’s inside, hackers learned which two lines going into the chip were the write protection and ground lines. By drilling through the chip, the lines would be destroyed and therefore unable to prevent the console from running burned discs. However, accidentally destroying any other lines in the chip could ruin your console’s DVD drive. Using a drill bit that was two large could do the same.
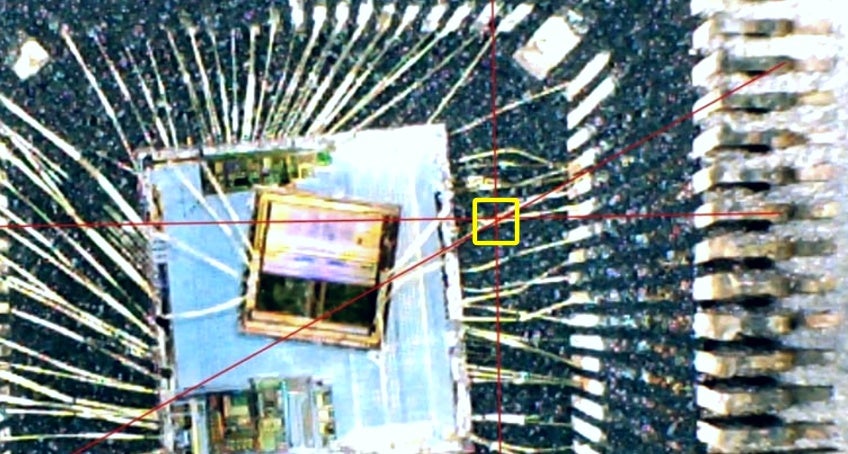
“Essentially, you have one chance,” said Modern Vintage Gamer. “And if you screwed it up, you’ve completely hosed your drive.”
The first hackers had to measure with rules and pencil lines on the chip to know where to drill. Guides appeared, and tools were inevitably created to help simplify the process and reduce risk. There were “Kamikaze Kits” that would tell pirates if they had drilled too far, destroying their drive.

Once the security measure was drilled it, hackers could flash the drive with custom firmware and play bootleg copies.
Hackers, it seems, always find a way.
For more on hacks and game history, check out Modern Vintage Gamer’s channel.

Leave a Reply